What is SIEM and How Does It Work?
In today’s increasingly digital world, cybersecurity has become a critical concern for organizations of all sizes. From small businesses to global enterprises, the need for robust security measures is undeniable. One of the most powerful tools in a company’s cybersecurity arsenal is SIEM – Security Information and Event Management. But what exactly is SIEM, and how does it work to protect organizations from cyber threats? Let’s dive in.
What is SIEM?
SIEM is a comprehensive cybersecurity solution that combines two crucial aspects: Security Information Management (SIM) and Security Event Management (SEM). In simple terms, SIEM systems collect, analyze, and correlate security data from various sources within an organization’s IT environment to detect, investigate, and respond to potential security incidents in real-time.
Breaking Down SIEM: SIM + SEM
- Security Information Management (SIM): This part of SIEM focuses on gathering and storing log data from multiple systems, including firewalls, servers, endpoints, and applications. It allows security teams to access historical data for trend analysis and compliance reporting.
- Security Event Management (SEM): This aspect deals with monitoring and analyzing events in real-time. SEM identifies suspicious activities, correlates events, and generates alerts that prompt immediate action when necessary.
By merging these two components, SIEM systems provide a unified view of an organization’s security landscape, making it easier for cybersecurity teams to identify, manage, and respond to threats efficiently.
How Does SIEM Work?
Now that we know what SIEM is, let’s explore how it works. At its core, SIEM operates through several interconnected processes:
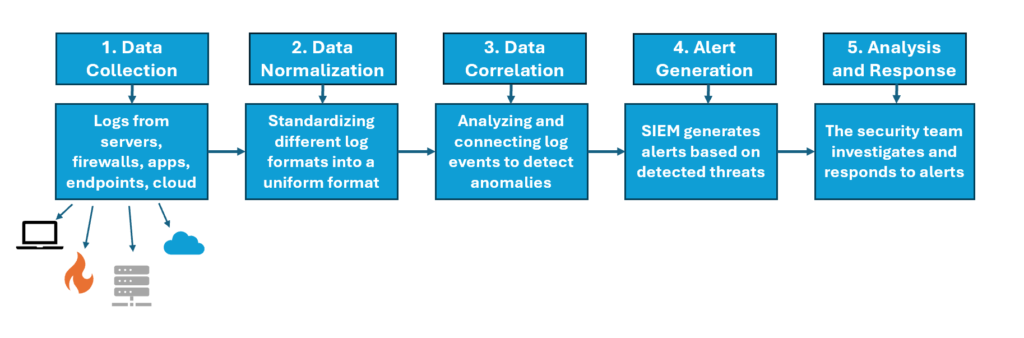
- Data Collection
- SIEM systems start by collecting vast amounts of log and event data from various sources such as firewalls, servers, operating systems, databases, and even cloud environments. This data provides valuable insights into user activities, network traffic, login attempts, file access, and other behaviors that could indicate potential threats.
- These logs are continuously fed into the SIEM system through connectors or agents that integrate with different devices and applications across the organization.
- Data Normalization
- Once the SIEM system collects the raw log data, it normalizes it. Normalization is the process of standardizing different log formats so that the data from diverse sources can be organized, structured, and interpreted consistently. For instance, logs from firewalls, servers, and endpoints may vary in structure, but SIEM converts them into a common format for easier analysis.
- Normalization ensures that no matter where the log data comes from, the SIEM system can analyze it cohesively and identify patterns that could signal a security incident.
- Data Correlation
- Correlation is one of the most critical functions of a SIEM system. It involves connecting the dots between various log events to identify patterns or anomalies that might indicate malicious activity.
- For example, a SIEM might correlate multiple failed login attempts from a single user account, followed by a successful login from an unfamiliar IP address. Individually, these events might not seem significant, but when correlated, they may indicate a potential brute-force attack or compromised credentials.
- This correlation process enables SIEM systems to detect threats that would otherwise go unnoticed if viewed as isolated incidents.
- Alert Generation
- When the SIEM system identifies an unusual pattern or potential threat, it generates an alert. These alerts are designed to notify the security team of suspicious activities in real-time, allowing them to take immediate action.
- Alerts are often ranked based on severity levels, such as low, medium, high, or critical. This prioritization helps security teams focus on the most urgent threats first, ensuring that critical incidents receive attention as quickly as possible.
- Analysis and Investigation
- After an alert is triggered, the security team uses the SIEM system’s dashboard and analysis tools to investigate the event further. SIEM platforms offer visualizations, timelines, and comprehensive reports that provide insights into the context and potential impact of the incident.
- With this data, the team can determine whether the alert is a false positive or a legitimate threat. If it’s a confirmed threat, the next step is remediation.
- Response and Remediation
- A modern SIEM solution may also integrate with Security Orchestration, Automation, and Response (SOAR) platforms, enabling automated responses to certain types of incidents. For example, if a SIEM detects a suspicious login from a known malicious IP address, it could automatically block the IP or disconnect the compromised device from the network.
- If automation isn’t in place, the security team can manually respond based on predefined protocols, such as isolating affected systems, initiating backups, or alerting relevant personnel.
- Reporting and Compliance
- SIEM systems not only detect and respond to threats but also generate detailed reports for compliance and auditing purposes. Many industries and regulations (like GDPR, HIPAA, and PCI-DSS) require organizations to maintain logs and demonstrate that they have effective security measures in place.
- SIEM platforms simplify this by providing pre-configured reports that showcase compliance with specific standards, making it easier for organizations to prove adherence during audits.
Example of a SIEM Alert
When an abnormal event occurs, such as an unauthorized login attempt, the SIEM generates an alert that contains specific details about the incident. Below is an example of what a SIEM alert might look like.
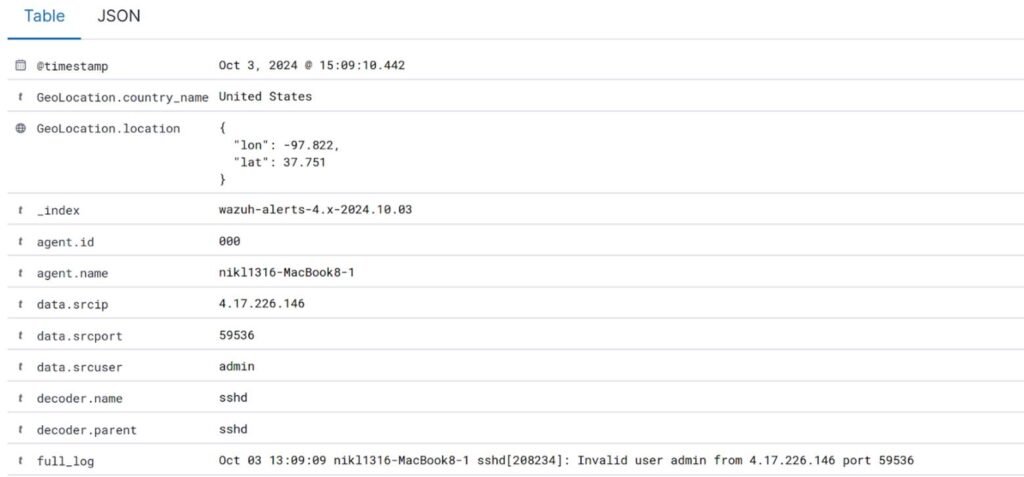
Let’s break it down:
- Timestamp: Indicates when the event was detected. For example:
- Oct 3, 2024 @ 15:09:10.442
- Geolocation: The SIEM might provide geographical information about the source of the activity:
- Country: United States
- Location: Latitude: 37.751, Longitude: -97.822
- Agent Information: Details about the system or endpoint where the alert originated:
- Agent ID: 000
- Agent Name: nikl1316-MacBook8-1
- Source Information: Details of the source attempting to connect:
- IP Address: 4.17.226.146
- Port: 59536
- User: admin
- Decoder Information: Indicates which security component or service detected the event:
- Decoder Name: sshd (Secure Shell Daemon)
- Event Details: A full log entry capturing the specific details of the event:
- Full Log: “Oct 03 13:09:09 nikl1316-MacBook8-1 sshd[208234]: Invalid user admin from 4.17.226.146 port 59536”
Why is SIEM Important for Organizations?
According to recent estimates, there are over 2,200 cyber attacks happening every single day. SIEM has therefore become an essential tool for modern cybersecurity because it provides several key benefits:
- Centralized Visibility: SIEM solutions consolidate security data from across the organization, providing a centralized view of the entire IT environment. This visibility is crucial for detecting threats quickly and responding to them effectively.
- Threat Detection and Incident Response: By correlating data in real-time, SIEM systems enable early detection of suspicious activities and automate responses, reducing the potential damage from cyber incidents.
- Regulatory Compliance: With its logging, monitoring, and reporting capabilities, SIEM helps organizations meet various compliance requirements, making it easier to pass audits and avoid penalties.
- Reduced Alert Fatigue: Modern SIEM solutions use advanced filtering and correlation techniques to reduce false positives, ensuring that security teams can focus on genuine threats rather than being overwhelmed by a flood of alerts.
Conclusion
In a landscape where cyber threats are becoming more sophisticated and frequent, SIEM stands out as a crucial component of an organization’s cybersecurity strategy. By providing real-time visibility, advanced threat detection, and automated response capabilities, SIEM empowers security teams to act quickly and protect critical assets. Whether you’re a small business or a large enterprise, understanding and implementing SIEM can be the difference between a minor security incident and a major data breach.
If your organization is looking to enhance its cybersecurity posture, investing in a SIEM solution might just be the next step you need to take.