How to Brute Force SSH Using Hydra

Brute forcing SSH login credentials is a common method used by attackers to gain unauthorized access to systems. While it’s essential to understand the security risks associated with SSH brute forcing, it’s equally important to know how attackers use tools like Hydra for educational purposes and to secure your own systems.
In this post, we will explain how to brute force SSH using Hydra, which is a powerful password-cracking tool. This guide is meant for ethical hacking, penetration testing, and security auditing. Always ensure you have permission before attempting any security tests.
What is Hydra?
Hydra is a widely used tool for cracking login credentials through brute force attacks. It supports a wide variety of services, including SSH, FTP, SMTP, HTTP, and more. Hydra performs a dictionary attack using a list of possible usernames and passwords to try against a login service.
Step 1: Install Hydra
If Hydra is not already installed on your machine, you’ll need to install it first.
sudo apt-get update
sudo apt-get install hydraStep 2: Obtain or Create a Wordlist
A wordlist is crucial for the brute force process as it contains possible username/password combinations. You can use wordlists like RockYou (often found in /usr/share/wordlists/rockyou.txt on Kali Linux) or create your own custom wordlist depending on the target’s environment.
You can find large collections of wordlists on GitHub or use the famous SecLists repository:
git clone https://github.com/danielmiessler/SecLists.gitStep 3: Identify the Target SSH Server
For demonstration purposes, let’s assume the target SSH server’s IP address is 192.168.1.100. Ensure the target system has SSH enabled and is listening on port 22 (the default SSH port).
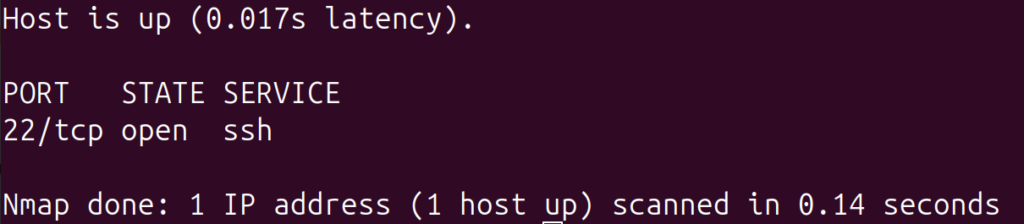
You can use Nmap to confirm that SSH is active on the target:
nmap -p 22 192.168.1.100
If SSH is active, you should see output similar to this:
Step 4: Start the Brute Force Attack
Now that we have Hydra installed, a wordlist, and an identified target, let’s start the brute force attack.
In this example, we’ll use the username root (replace with the username you’re targeting) and the RockYou wordlist for passwords.
Run the following Hydra command:
hydra -l root -P path/to/wordlist.txt ssh://192.168.1.100
Breakdown of the Command:
-l root: Specifies the username (rootin this case).-P path/to/wordlist.txt: Specifies the path to the password wordlist.ssh://192.168.1.100: Specifies the target SSH service and its IP address.
Hydra will now start attempting to brute force the SSH login by trying each password from the wordlist for the root user.
Note:
It is also possible to brute force the username with the -L command if you know the password. It’s also possible to brute force both the username and password, this will just heavily increase the run time of the attack. Example seen below.
hydra -L /path/to/usernames.txt -P /path/to/passwords.txt ssh://192.168.1.100Step 5: Monitor the Output
Hydra will try each password from the wordlist and display the results in your terminal. If it finds the correct password, it will output the successful username and password combination, like so:
[22][ssh] host: 192.168.1.100 login: root password: password123At this point, Hydra has successfully found the credentials for the target system.
Step 6: Prevent SSH Brute Force Attacks
Now that you’ve seen how easy it can be to brute force SSH using Hydra, it’s critical to understand how to secure your systems from similar attacks.
Here are some best practices to protect your SSH servers:
- Disable Root Login: Edit the SSH configuration file
/etc/ssh/sshd_configand setPermitRootLogin noto prevent root logins over SSH. - Use Strong Passwords: Always use complex, unique passwords that are difficult to guess or brute force.
- Enable SSH Key Authentication: Replace password-based authentication with SSH key-based authentication. This requires an attacker to have both the private key and the passphrase to log in.
- Limit Login Attempts: Use tools like
fail2banto block IP addresses after several failed login attempts. - Use Non-Standard SSH Ports: Change the default SSH port from
22to a higher, less obvious port. While this is not foolproof, it adds an extra layer of obscurity. - Monitor Logs: Regularly check SSH logs (
/var/log/auth.log) for suspicious activity, or alternatively install a SIEM solution.
Step 7: Changing Port Number
To use Hydra on a non-default SSH port (any port other than the default 22), you can specify the custom port directly in the Hydra command using the -s option.
Let’s assume the SSH server is running on port 2222 (replace this with your actual port), and the target SSH server is running on 192.168.1.100. The command will then look like this:
hydra -L /path/to/usernames.txt -P /path/to/passwords.txt -s 2222 ssh://192.168.1.100Conclusion
Hydra is a powerful tool for brute forcing SSH and other network services, but it also highlights the importance of securing your servers. By learning how these attacks work, you can better defend against them and ensure your systems are safe.
Always remember, this guide is for educational purposes only and should be used responsibly.
Happy hacking!