The OSI Model and Cyber Attacks Against its Layers

In the world of networking, the OSI (Open Systems Interconnection) Model is fundamental to understanding how data is transmitted between devices. By breaking down network communications into seven distinct layers, the OSI model simplifies the process of troubleshooting and analyzing network issues.
However, these same layers also present distinct entry points for cyberattacks. Each layer is susceptible to specific vulnerabilities, and knowing how attacks occur on each one can significantly enhance security strategies.
In this post, we’ll dive into the OSI model’s seven layers and explore the types of cyberattacks that commonly target each.
Overview of the OSI Model
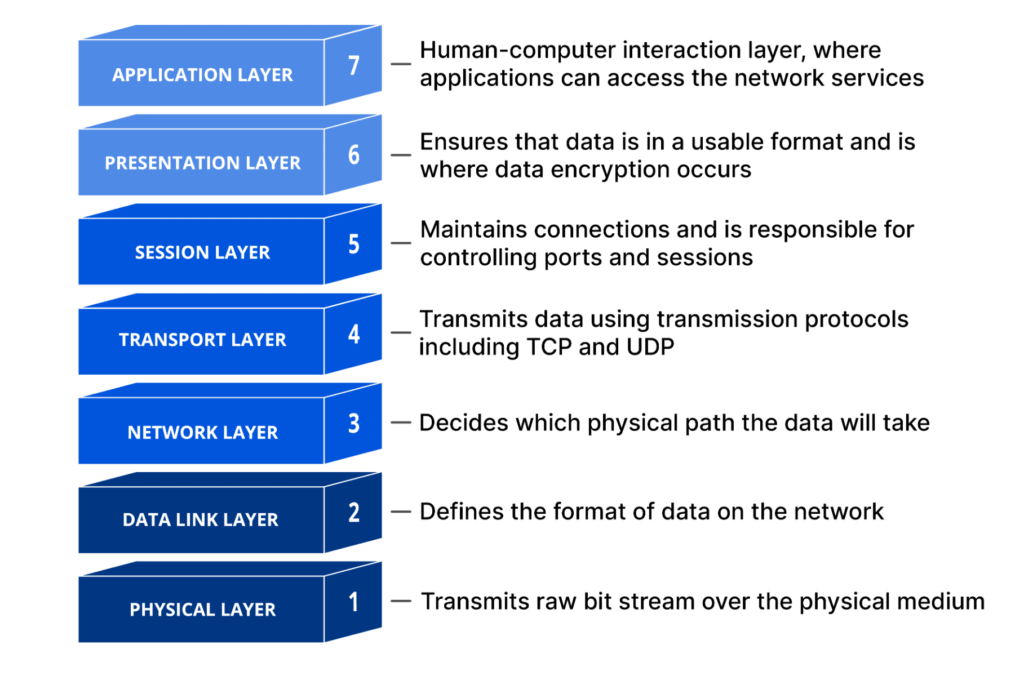
The OSI model is divided into seven layers, each responsible for a different aspect of network communication:
- Physical Layer (Layer 1): Handles the physical connection between devices, such as cables, switches, and hardware.
- Data Link Layer (Layer 2): Manages the direct data transfer between devices over a physical link, including error detection and handling.
- Network Layer (Layer 3): Routes data from one network to another, determining the best path for data transmission.
- Transport Layer (Layer 4): Ensures reliable data transfer, including error recovery and flow control, often using protocols like TCP/UDP.
- Session Layer (Layer 5): Manages the sessions or connections between applications, ensuring proper synchronization and dialog control.
- Presentation Layer (Layer 6): Translates and formats data so it can be understood by the application layer. It handles encryption, compression, and translation of data formats.
- Application Layer (Layer 7): Provides end-user services like email, file transfer, and web browsing.
Visual representation of the OSI model.
Cyberattacks by OSI Layer
1. Physical Layer Attacks
The physical layer is often considered the most basic, but it’s still vulnerable to attacks that disrupt or tamper with hardware infrastructure. Cyberattacks at this layer target physical components of the network.
- Wiretapping: Involves physically intercepting and listening to network communications through compromised cables or devices.
- Signal Jamming: Interferes with wireless signals, such as Wi-Fi, to disrupt communications.
- Hardware Tampering: Attackers physically alter or damage network devices like routers or switches, leading to network outages or vulnerabilities.
Defense Strategy: Employing physical security measures such as surveillance cameras, secure data centers, tamper-proof equipment, and shielding to prevent jamming attacks.
2. Data Link Layer Attacks
The data link layer controls data exchange between two connected devices. Vulnerabilities in this layer can be exploited by cybercriminals to disrupt or manipulate communication.
- MAC Spoofing: Attackers alter their Media Access Control (MAC) address to impersonate a legitimate device on the network.
- ARP Spoofing (Address Resolution Protocol): Manipulates the ARP tables to associate an attacker’s MAC address with a legitimate IP address, leading to data interception.
Defense Strategy: Implement network segmentation, switch port security, and use static ARP entries to prevent spoofing attacks.
3. Network Layer Attacks
The network layer manages data routing between devices across different networks. It is a prime target for attackers looking to disrupt traffic or eavesdrop on communications.
- IP Spoofing: Attackers forge the source IP address of a packet to disguise their identity or impersonate another system.
- DDoS (Distributed Denial of Service): Overloads a network by flooding it with excessive traffic, making it unavailable to legitimate users.
- Routing Attacks: Exploit weaknesses in routing protocols, such as BGP hijacking, to redirect traffic to malicious destinations.
Defense Strategy: Use firewalls, intrusion detection systems, and rate limiting to mitigate DDoS and spoofing attacks. Implement secure routing protocols to protect against hijacking.
4. Transport Layer Attacks
The transport layer ensures reliable data transmission, but attackers often exploit its protocols (like TCP and UDP) to disrupt or intercept communication.
- TCP SYN Flood: Attackers send numerous SYN requests to a server but do not complete the handshake, overwhelming the system and causing denial of service.
- UDP Flood: Sends a large number of UDP packets to random ports, consuming resources and bandwidth.
Defense Strategy: Employ firewalls, SYN cookies, and rate-limiting techniques to protect against flood attacks. Also, enable TCP sequence number randomization to prevent spoofing.
5. Session Layer Attacks
The session layer establishes and maintains connections between devices, which can be exploited by attackers to hijack or disrupt sessions.
- Session Hijacking: Attackers steal a session token or session ID to gain unauthorized access to a user’s active session.
- SSL/TLS Attacks: Target vulnerabilities in Secure Sockets Layer (SSL) or Transport Layer Security (TLS), such as weak encryption algorithms, to intercept encrypted data.
Defense Strategy: Use strong encryption, secure session management, and timeouts for inactive sessions. Regularly update SSL/TLS protocols to the latest versions.
6. Presentation Layer Attacks
The presentation layer deals with data translation and encryption. Poor handling of data formatting or encryption can expose vulnerabilities.
- Man-in-the-Middle (MITM): Attackers intercept and manipulate data being transmitted between two parties.
- Code Injection: Malicious code is inserted into data fields that are poorly sanitized, leading to potential exploitation of the application or system.
Defense Strategy: Implement robust data validation, secure encryption standards, and proper input sanitization to prevent MITM and injection attacks.
7. Application Layer Attacks
The application layer is the most exposed layer, interacting directly with end users. It is often targeted by attackers using a wide array of sophisticated techniques.
- SQL Injection: Malicious SQL queries are injected into web forms to gain unauthorized access to databases.
- Cross-Site Scripting (XSS): Injects malicious scripts into web applications that are then executed in users’ browsers.
- Phishing: Tricks users into revealing sensitive information by impersonating legitimate services.
- DNS Attacks: Manipulates DNS queries to redirect users to malicious websites (DNS poisoning).
Defense Strategy: Regularly patch software and web applications, conduct security audits, and use web application firewalls (WAFs) to detect and block attacks. Educate users about phishing and social engineering threats.
The OSI Model: A Layered Approach to Cybersecurity
Understanding the OSI model not only helps in diagnosing networking issues but also in recognizing how cyberattacks can occur at each layer. By taking a layered approach to cybersecurity—employing physical security, encryption, secure routing, firewalls, and user education – you can significantly reduce the attack surface. Cybersecurity professionals should consistently monitor each layer for vulnerabilities and implement robust security measures to protect against a wide range of threats.
In the world of networking and cybersecurity, a proactive stance is key to defending against evolving attack methods that exploit OSI layer vulnerabilities. Want to learn more about Cyber Security and How to Master It? Check out our ultimate guide.